Protecting your sensitive information and essential technology from cyberattacks is a key factor in your organization’s survival. This is where strategic cyber risk management comes in.
A solid cyber risk management strategy helps build strong defenses against cyber threats without hindering your business’s growth. It not only enhances security but also ensures that your business stays compliant with regulations.
In this article, we’ll explain the fundamental principles of cyber risk management and demonstrate how integrating it with a simple yet effective security framework can lead to strategic success.
Key Points of Risk-Based Cybersecurity in Simple Terms
- Reducing Risks: Actively identifying and neutralizing threats before they occur helps minimize the potential impact of a cyber incident.
- Focused Investment: By recognizing and assessing risks, you can concentrate your investment efforts on the areas that need attention the most.
- Addressing Critical Risks First: Tackling the most severe vulnerabilities first strengthens your business’s overall security.
Introducing Cyber Risk Management Frameworks
Cybersecurity risk frameworks act as guides that help businesses implement a risk-based approach effectively. Here’s how they can benefit your business:
- Remove Guesswork: Frameworks provide a structured way to evaluate your current cybersecurity status.
- Systematic Focus: They help organizations systematically direct their investments toward addressing the most critical risks.
- Guidance for Building Security: Frameworks offer the right guidance to build security, which is crucial for earning customer trust.
- Tested Controls: Built with tried and tested controls, frameworks assist businesses in implementing effective security measures.
- Compliance Assistance: Frameworks are designed to help businesses comply with government and industry regulations.
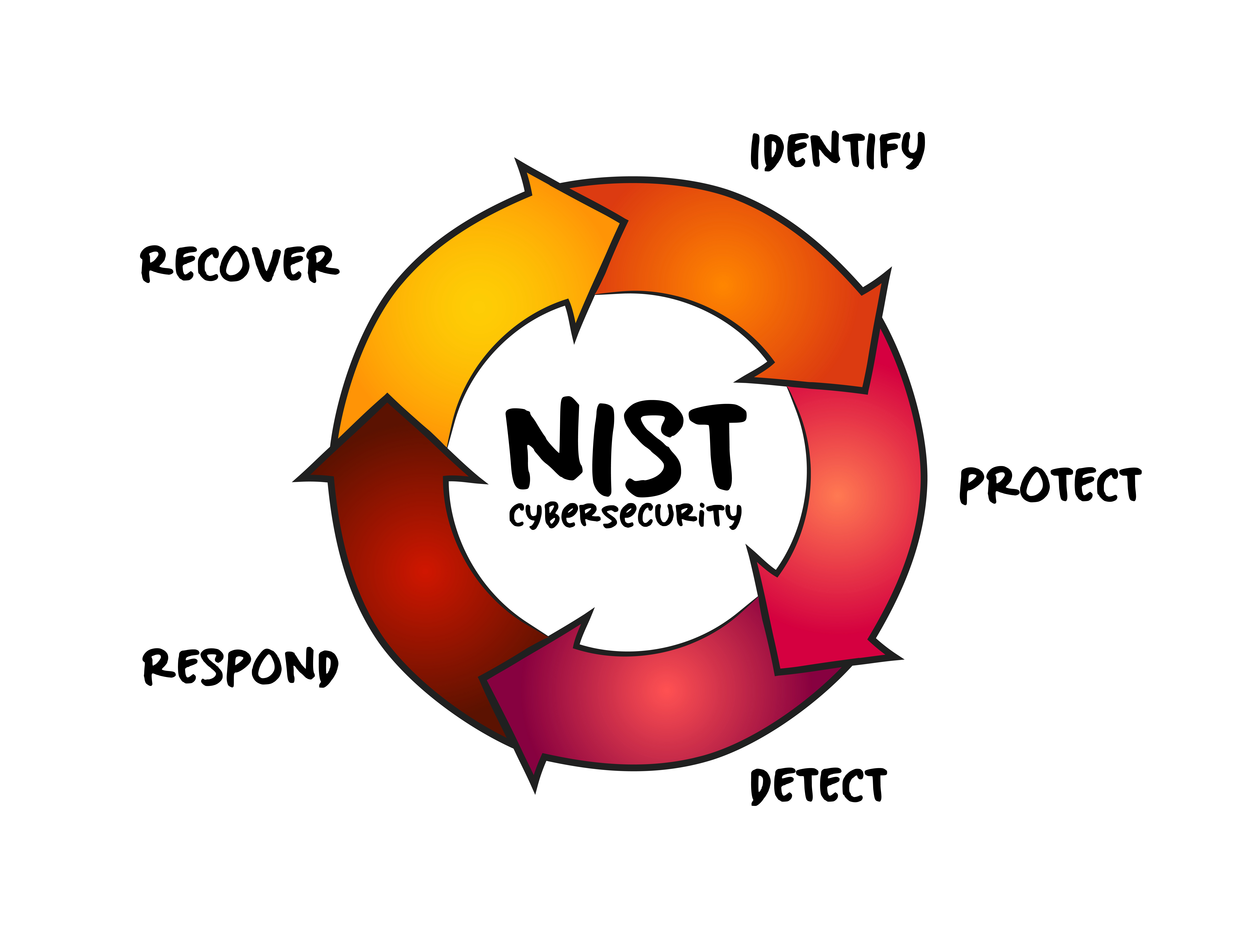
NIST Cybersecurity Framework Simplified
The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is is a user-friendly framework that empowers business leaders to enhance organizational cybersecurity. Here’s how it supports a risk-based approach:
- Identify: It helps you understand the risks around what is most valuable to your business.
- Protect: Provides an overview of people, processes, technology, and information that need protection for successful business operations.
- Detect: Promotes continuous monitoring and adaptation to evolving threats.
- Respond: Creating an incident response plan is key to minimizing downtime and reducing stress during a crisis.
- Recover: A step by step recovery plan will simplify the recovery process and keep stakeholders updated.
 Conclusion:
Conclusion:
Safeguarding your business from cyber threats is vital for its survival and growth. Rather than leaving your business security to chance, consider partnering with an experienced IT service provider like Claritech. We use these tools every day and can help you navigate the complex world of standards and compliance. Contact us now!




